Integration Development: Support for JWT Bearer Tokens for Client Authentication
In previous versions of MYOB Acumatica, for a client application that implements the OAuth 2.0 or OpenID Connect (OIDC) authorization mechanism, only shared secrets were available. That is, a developer registered the client application on the Connected Applications (SM303010) form to create a shared secret, which is a secret key that is stored both in the MYOB Acumatica instance and in the client application.
MYOB Acumatica 2024.1.1 implements support for JSON Web Token (JWT) Bearer Tokens for client authentication. With this support, the private secret key is stored only in the client application, while the MYOB Acumatica instance holds the public key.
For a client application to use the new functionality, the developer needs to do the following:
- Add a JSON Web Key (JWK) or a URL for JSON Web Key Set (JWKS URL) for the application on the Connected Applications (SM303010) form, as described in the following section.
- In the client application, implement support of JWT, as described below.
- Include the information about the connected application in the customization project.
For a detailed description of OAuth 2.0 or OIDC mechanism of authorization, see OAuth 2.0 and OIDC: General Information
Registration of the Application on the Connected Applications Form
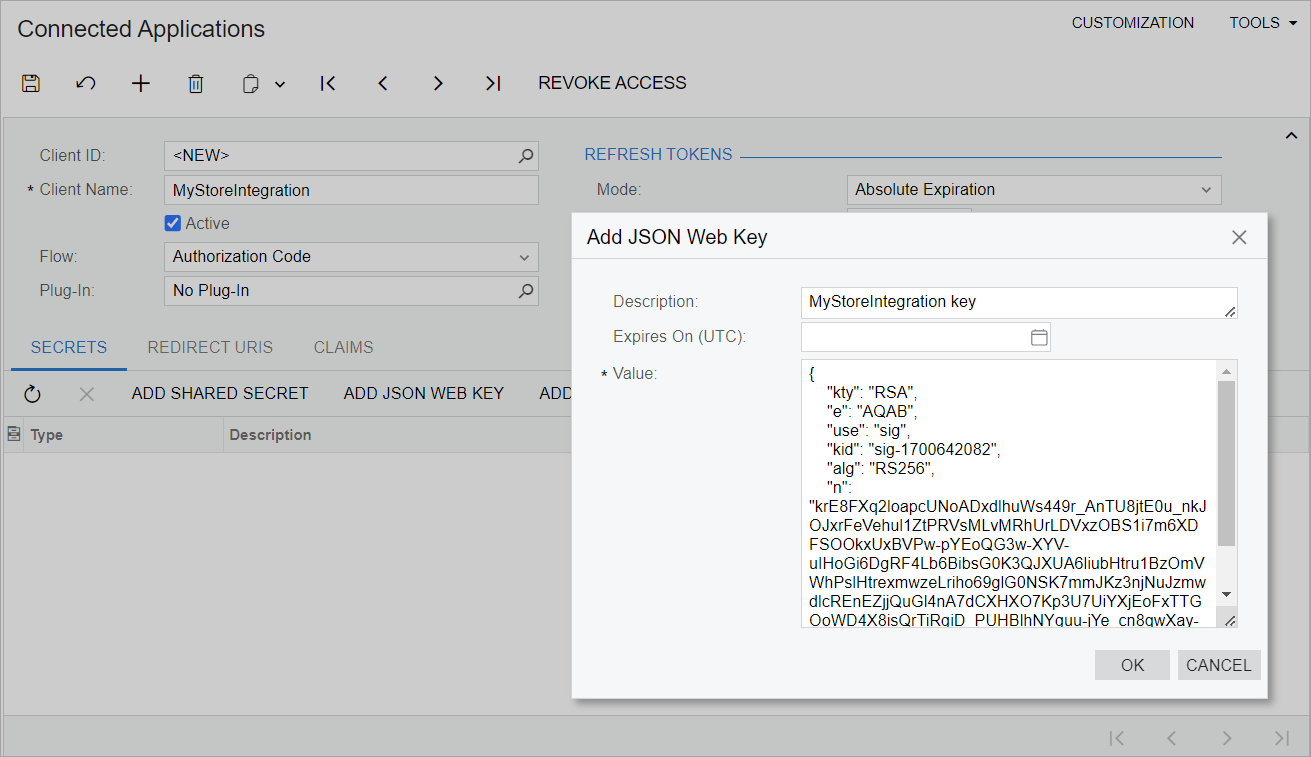
When a developer registers the application on the Connected Applications (SM303010) form, the developer adds either a JWK or an JWKS URL on the Secrets tab.
To add a JWK, the developer clicks the new Add JSON Web Key button on the table toolbar. The developer specifies the needed data in the dialog box that opens, as shown in the following screenshot. For JWK, MYOB Acumatica supports the format that is defined in RFC7517 (https://datatracker.ietf.org/doc/html/rfc7517#section-4).
- It is accessible from each MYOB Acumatica instance that is used with the client application. If the location is inaccessible, the token request is declined with the invalid_client error.
- It complies with RFC7515 (https://datatracker.ietf.org/doc/html/rfc7517#section-5).
- It should support a reasonable load because each MYOB Acumatica instance that is used with the client application will access this location on every token request.
For details about registration of client applications in MYOB Acumatica, see Registration of an OAuth 2.0 or OIDC Application: General Information.
JWT Support in the Client Application
In the client application, a developer implements support of JWT, as described in https://www.rfc-editor.org/rfc/rfc7523.html#section-2.2. JWT can be implemented for any flow that is supported by MYOB Acumatica for client authentication.
The following diagram shows the authorization code flow that uses JWT.
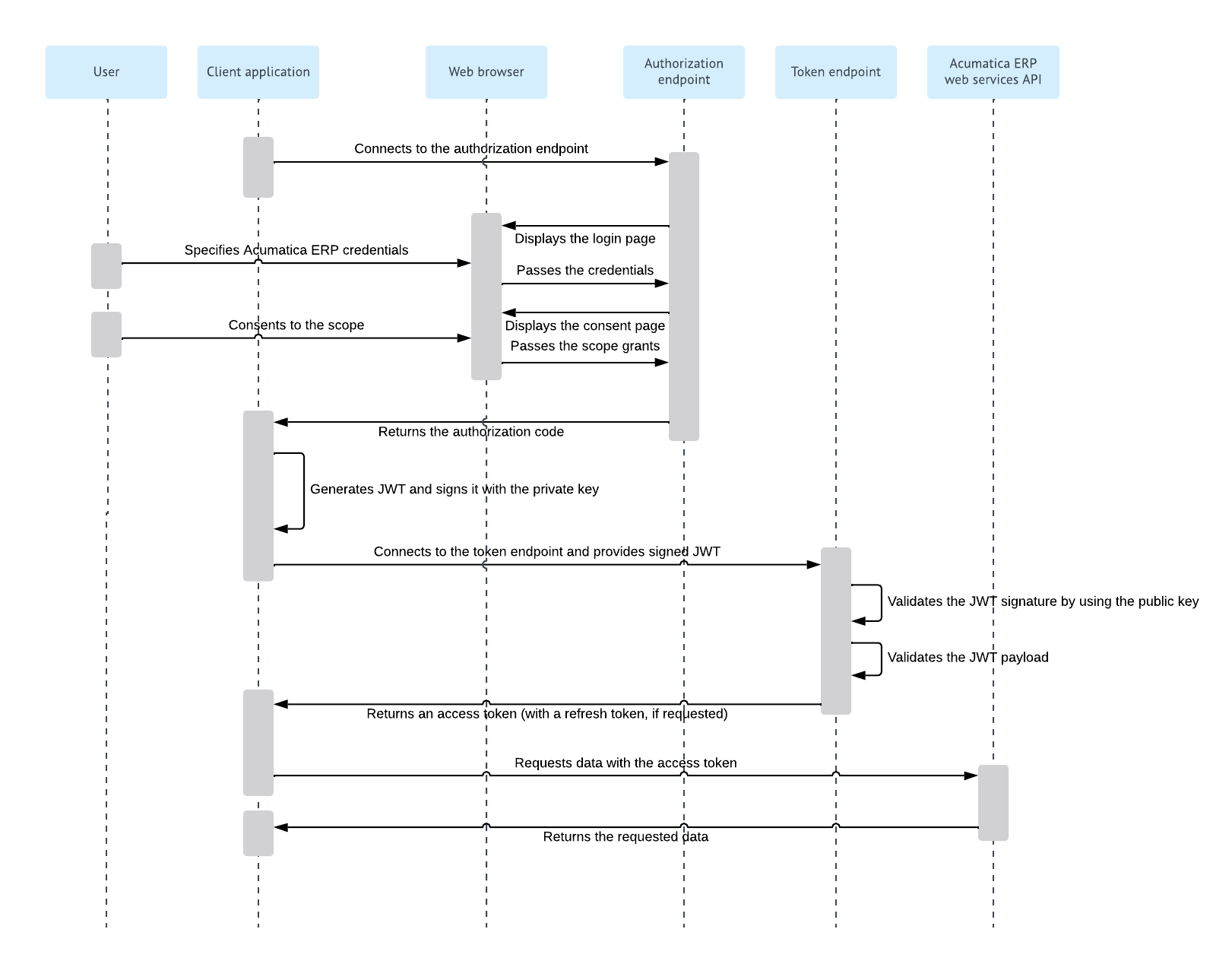
For implementation details, see Authorization Code Flow: General Information, Resource Owner Password Credentials Flow: General Information, and Hybrid Flow: General Information.