Resource Owner Password Credentials Flow: General Information
When you implement OAuth 2.0 in a client application to make the application work with MYOB Acumatica, you can use the Resource Owner Password Credentials flow.
With the Resource Owner Password Credentials flow, the credentials (username and password) of the MYOB Acumatica user are provided directly to the client application, which uses the credentials to obtain the access token. When the access token expires, the client application can request a new access token by providing a refresh token.
Learning Objectives
In this chapter, you will learn how to implement a client application that uses the Resource Owner Password Credentials flow.
Applicable Scenarios
You can use the Resource Owner Password Credentials flow in environments where the client application can securely store user credentials and there is a high level of trust between the user and the client application, as with native mobile applications.
- Handling and transmitting user credentials directly from the client application to the authorization server can introduce security risks.
- Because the Resource Owner Password Credentials flow bypasses the authorization step, a user does not have the opportunity to review and grant consent to the client application's access to the resources.
Therefore, you should carefully consider the use of the Resource Owner Password Credentials flow, and prefer other authorization flows, such as Authorization Code flow, whenever possible.
Resource Owner Password Credentials Flow
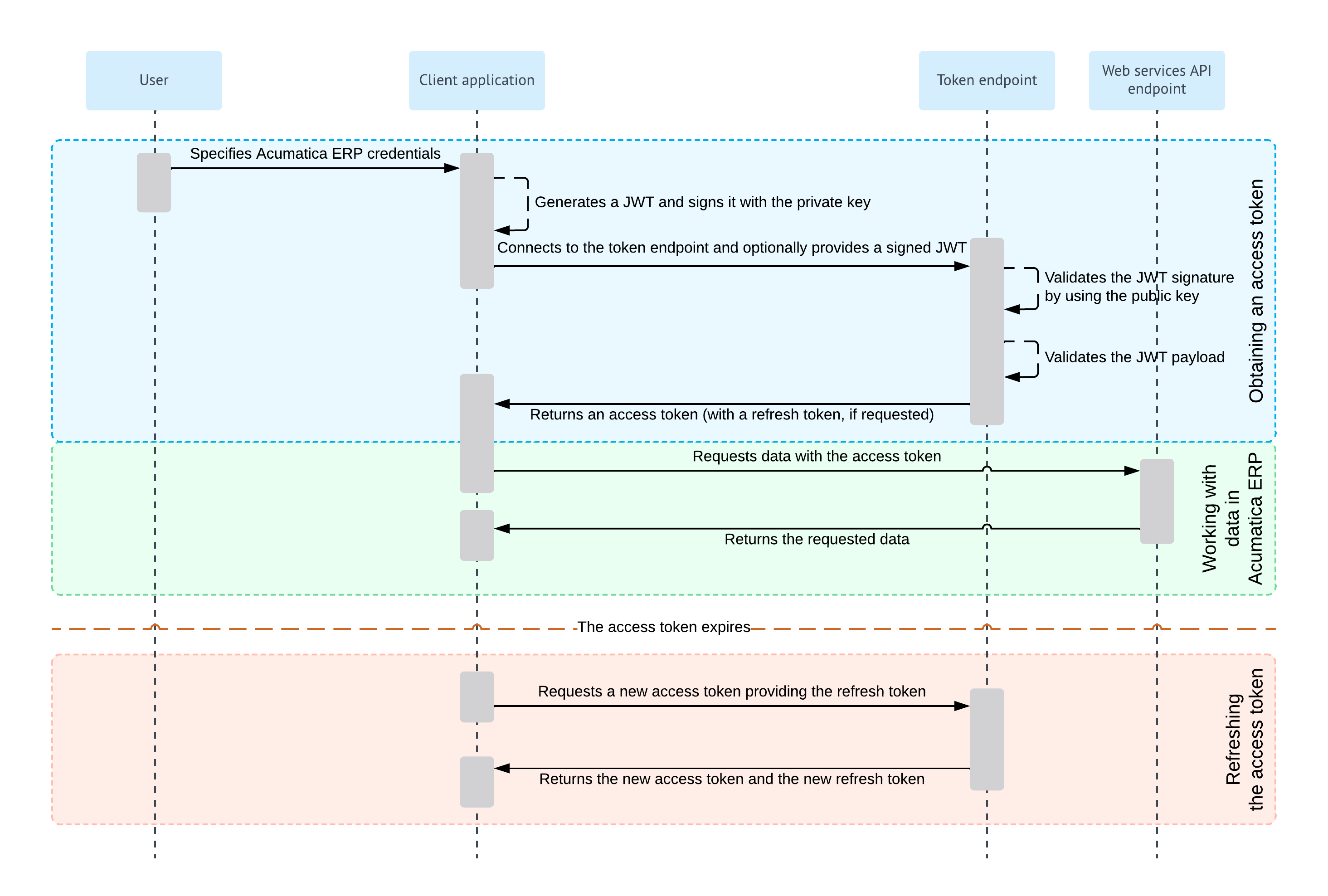
For the support of the Resource Owner Password Credentials flow, you implement the following general steps in the application:- Obtaining an access token
The client application obtains the username and password of the applicable MYOB Acumatica user, which can then be exchanged for an access token.
If the client application uses JSON Web Token (JWT) bearer tokens, the application generates a JWT and signs it with the private key.
The client application connects to the token endpoint of MYOB Acumatica, submits the user credentials, and provides a signed JWT or a shared secret. If a JWT is provided, MYOB Acumatica verifies the JWT signature by using the public key (which was specified during the registration of the client application in MYOB Acumatica) and validates the JWT payload. If a shared secret is provided, MYOB Acumatica verifies the provided application credentials.
If verification is completed successfully, MYOB Acumatica issues an access token, which the client application should provide with each data request to MYOB Acumatica, and a refresh token (if requested).
For more information on this process, see Resource Owner Password Credentials Flow: Obtaining of an Access Token.
- Optional: Working with data in MYOB Acumatica
The client application requests data from MYOB Acumatica and provides the access token with this request. MYOB Acumatica returns the requested data. For details on this process, see OAuth 2.0 and OIDC: Working with Data in MYOB Acumatica.
When the access token expires, the client application can request a new access token by providing a refresh token, as described in OAuth 2.0 and OIDC: Refreshing of an Access Token.
For details on the OAuth 2.0 authorization mechanism, see the specification at https://tools.ietf.org/html/rfc6749.
Diagram of the Resource Owner Password Credentials Flow