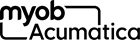Implicit Flow: General Information
When you implement OAuth 2.0 or OpenID Connect (OIDC) in a client application to make the application work with MYOB Acumatica, you can use the Implicit flow, which is a simplified variant of the Authorization Code flow.
With the Implicit flow, the client application never gets the credentials of the applicable MYOB Acumatica user. When the user is authenticated in MYOB Acumatica, the client application does not receive an authorization code (as with the Authorization Code flow); instead, the client application directly receives an access token, and then uses the access token to work with data in MYOB Acumatica. The access token is valid for a limited period of time and cannot be renewed.
Learning Objectives
In this chapter, you will learn how to implement a client application that uses the Implicit flow.
Applicable Scenarios
You implement the Implicit flow in a client application when you want to securely obtain an access token without exposing the user's credentials to the client application. This flow can be used for clients using a scripting language (such as JavaScript) or for mobile clients.
Implicit Flow
For the support of the Implicit flow, you implement the following general steps in the application:
- Obtaining an access token
The client application connects to the authorization endpoint of MYOB Acumatica.
The authorization endpoint directs the user of the client application to the sign-in page of MYOB Acumatica, where the user should enter the credentials to sign in to a tenant configured in the MYOB Acumatica instance.
Note:The user must sign in to the tenant that was specified in the client_id URL parameter passed to the authorization endpoint. (This tenant is selected by default on the sign-in page.)If the credentials are accepted by MYOB Acumatica, the system displays the consent form, where the user can confirm that the application has access to the requested scopes. Only the scopes that were requested by the application are displayed on the consent form.
Once the user grants access to the requested scopes, MYOB Acumatica issues the access token and the ID token (if requested). The client application should provide the access token with each data request to MYOB Acumatica.
If the ID token is retrieved, the client application validates it by using the key that is available on the OpenID Connect Preferences (SM303030) form. The client application can obtain the key through a
GETrequest to the following URL: [<MYOB Acumatica instance URL>]/identity/.well-known/openid-configuration/jwks. The ID token contains the claims to which the user has granted access.For more information on the request that obtains the tokens, see Implicit Flow: Obtaining of an Access Token and ID Token.
- Optional: Retrieving the user
information
The client application requests user information from MYOB Acumatica and provides the access token with this request. MYOB Acumatica returns the information for which the user has provided the consent. For details about this request, see OAuth 2.0 and OIDC: Obtaining of the User Data.
Attention:The recommended way of obtaining the user data is to parse the validated ID token, which contains the same claims as the ones that are obtained through this request. - Optional: Working with data in MYOB Acumatica
The client application requests data from MYOB Acumatica and provides the access token with this request. MYOB Acumatica returns the requested data. For details on this process, see OAuth 2.0 and OIDC: Working with Data in MYOB Acumatica.
For details on the OAuth 2.0 authorization mechanism, see the specification at https://tools.ietf.org/html/rfc6749. For details on the OIDC authorization mechanism, see the specification at https://openid.net/specs/openid-connect-core-1_0.html#Authentication.
Implicit Flow Diagram